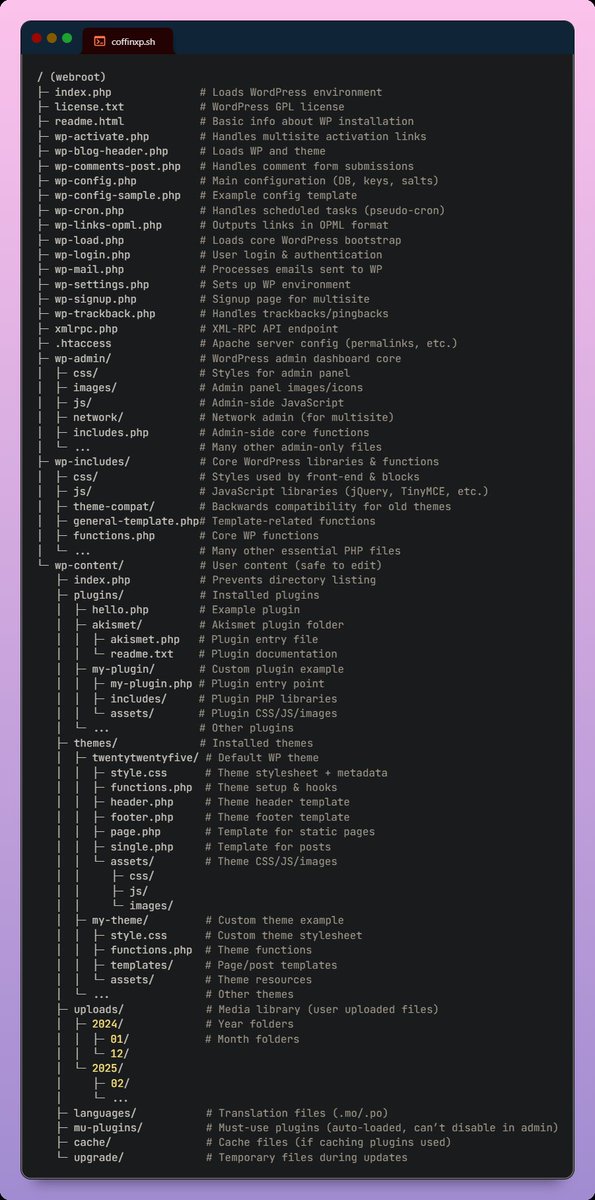
Double Tape @tape_double
Joined May 2024-
Tweets216
-
Followers7
-
Following458
-
Likes230
Trends for United States
481 B posts
35,1 B posts
46,1 B posts
92,7 B posts
1.833 posts
7.946 posts
108 B posts
33,8 B posts
40 B posts
3.805 posts
7.672 posts
28 B posts
3.631 posts
96,7 B posts
61,2 B posts
4.143 posts
41,6 B posts
7.649 posts
10,5 B posts